What Is Passwordless Authentication, And Why Does It Matter For Healthcare?
- The Bridge Team
- December 27, 2024
Passwordless authentication is a modern security method that eliminates the need for traditional passwords. Instead, it uses alternative credentials such as biometrics, one-time passcodes, or hardware tokens to verify a user’s identity. In healthcare, where safeguarding sensitive patient data is paramount, this approach offers enhanced security, improved usability, increased compliance, and reduced risks associated with password breaches.
At Bridge, we pride ourselves on being at the forefront of healthcare technology innovation. Our BridgeInteract patient engagement platform is designed from the ground up to be secure without sacrificing accessibility. Let’s explore why passwordless authentication is the new gold standard in healthcare and how you can implement it in your organization.
Want to learn more about the BridgeInteract patient engagement suite?
Jump to:
- What Is Passwordless Authentication?
- Why Use Passwordless Authentication?
- Advantages Of Passwordless Authentication In Healthcare Technology
- Why Healthcare Needs Passwordless Authentication Solutions
- How BridgeInteract Implements Passwordless Authentication
- How To Implement Passwordless Authentication In Healthcare Settings
- Get A Secure Patient Engagement Platform
What Is Passwordless Authentication?
Passwordless authentication refers to a login process that allows users to access systems without entering a password.
Unlike traditional authentication methods, it uses verification factors like:
- Biometric data (e.g., facial recognition or fingerprint scanning)
- One-Time Passwords (OTPs) sent to a registered device
- Magic links (unique, time-sensitive links) delivered through email
- Hardware tokens like security cards or USB keys
- Mobile authentication apps for push notifications
By eliminating static passwords and verifying a user using their own body (biometrics) or trusted devices, passwordless authentication reduces the risks of phishing, password theft, and data breaches.
Why Use Passwordless Authentication?
Simply put, password-based authentication systems are not well suited to human nature and have several inherent weaknesses. These include:
- Weak passwords: Many users create simple, easily guessable passwords (e.g., “123456” or “password”), which makes it easy for attackers to compromise accounts through brute-force techniques.
- Reuse across multiple sites: Users often reuse the same password across multiple sites. If one site is compromised, attackers can use the same credentials to access other accounts.
- Phishing and social engineering attacks: Attackers imitate legitimate websites or services to trick users into revealing their passwords.
- Password cracking: Even if passwords are encrypted, weak encryption algorithms or unsalted hashes can allow attackers to reverse-engineer passwords using tools to crack them.
- Forgotten passwords: Users often forget passwords, requiring password recovery mechanisms that attackers can exploit through account recovery fraud.
- Keylogging and malware: Hidden software can capture passwords as they are typed, making even strong passwords vulnerable.
- Password storage vulnerabilities: If passwords are not properly stored (e.g., in plaintext or with weak encryption), a data breach can lead to mass exposure of user credentials.
- Scalability issues: Managing different passwords for different services can be difficult for users, leading to bad habits like writing down passwords or storing them insecurely.
- Difficulty in enforcing strong password policies: Organizations may struggle to enforce strong password policies, leading to inconsistent implementation and reduced security.
The above security flaws make password-protected systems inadequate for any organization, especially in a public-facing, sensitive, and highly regulated industry like healthcare. Instead, passwordless solutions are the new standard in cybersecurity.
Advantages Of Passwordless Authentication In Healthcare Technology
Passwordless authentication is particularly important for healthcare organizations that need to maintain the highest standard of data security while making their digital services accessible to patients who have varying levels of technical expertise and may have special requirements with additional security concerns (e.g., caregiver proxy access). Easy-to-use secure access is a crucial part of a successful digital front door strategy for healthcare providers that want to engage patients with their online tools.
Explore the potential of the Digital Front Door in healthcare.
Here’s how passwordless authentication helps healthcare organizations to stay relevant in today’s digital landscape:
-
Enhanced security
Healthcare organizations handle highly sensitive data such as medical histories, billing details, and personal patient information. Traditional passwords can be compromised through phishing, brute force attacks, or poor password management. Using passwordless authentication solutions for their admin panels, EHR access, patient portal, and other tools, healthcare systems significantly reduce the risk of unauthorized access and data breaches. Techniques like biometrics are nearly impossible to replicate, providing an extra layer of security.
-
Improved user experience
Remembering complex passwords and frequently changing them is a hassle for patients and healthcare staff. Passwordless systems make it easy to log in securely without remembering or resetting passwords. For instance, using facial recognition or a fingerprint scan to access records saves time and offers a smoother experience. This improved ease of use is particularly beneficial for elderly patients or those less familiar with technology. Learn more about how passwordless authentication streamlines user experience in healthcare.
-
Lower operational costs
Password management can be a costly process for healthcare providers. IT teams spend significant time resetting forgotten passwords and addressing security issues. Passwordless authentication reduces these support costs by eliminating password-related support tickets.
-
Compliance and regulatory benefits
Healthcare organizations are bound by strict regulations like HIPAA, which mandates the protection of patient information. Data protection is the healthcare provider’s responsibility, and failure to comply can incur severe financial penalties. Passwordless authentication helps meet compliance requirements by offering strong, multifactor authentication without the vulnerabilities associated with passwords. Additionally, it supports audit trails and secure access management, making it easier for healthcare providers to demonstrate compliance.
-
Minimizes human error
A common cause of data breaches is human error, such as using weak passwords or falling for phishing scams. Passwordless systems reduce this risk by removing the password component entirely. For example, if a clinician can log in using a secure biometric scan instead of typing in a password, the chance of unauthorized access due to weak or stolen passwords is virtually eliminated.
Why Healthcare Needs Passwordless Authentication Solutions
Healthcare providers are prime targets for cyberattacks because medical data is highly valuable on the black market. According to research, healthcare data breaches have been increasing year after year since 2015 and are among the costliest across all industries in the US, averaging $10 million per breach (1, 2).
Data breach costs can quickly spiral out of control as critical IT infrastructure is compromised. In March 2024, United Healthcare paid a $22 million ransomware demand, but the cost of system restoration, service interruption, and other damage control and repair efforts reportedly cost the company billions of dollars (3). Even without any cyberattack involved, healthcare providers can incur civil fines ranging from $141 to $71,162 per violation, depending on the level of culpability, as well as potential criminal penalties (4).
Passwordless authentication can mitigate these risks by removing one of the weakest links in security: traditional passwords.
- Prevent credential theft: Passwordless systems eliminate the threat of stolen or reused passwords, making it harder for attackers to access healthcare data.
- Ensure HIPAA compliance: HIPAA’s security rule mandates that covered entities implement mechanisms to ensure that only authorized individuals can access ePHI. Passwordless authentication helps your organization stay compliant and avoid the risk of violating HIPAA rules.
- Facilitate secure remote access: As telehealth becomes more prevalent, healthcare providers need secure ways to access patient data from remote locations. Passwordless authentication provides a reliable solution for secure remote logins. Bridge Virtual Care incorporates passwordless authentication for all users, including approved caregivers and family members, to offer a telehealth platform.
How BridgeInteract Implements Passwordless Authentication
The BridgeInteract patient engagement platform integrates passwordless authentication solutions to support secure, frictionless access for healthcare providers and patients without compromising user experience.
Key Features Of Bridgeinteract’s Passwordless Authentication:
- Single sign-on (SSO) capabilities
BridgeInteract uses passwordless SSO to streamline access across multiple healthcare systems. With SSO, users can securely log in once and gain access to all linked healthcare applications, eliminating the need to remember multiple passwords. - Biometric login options
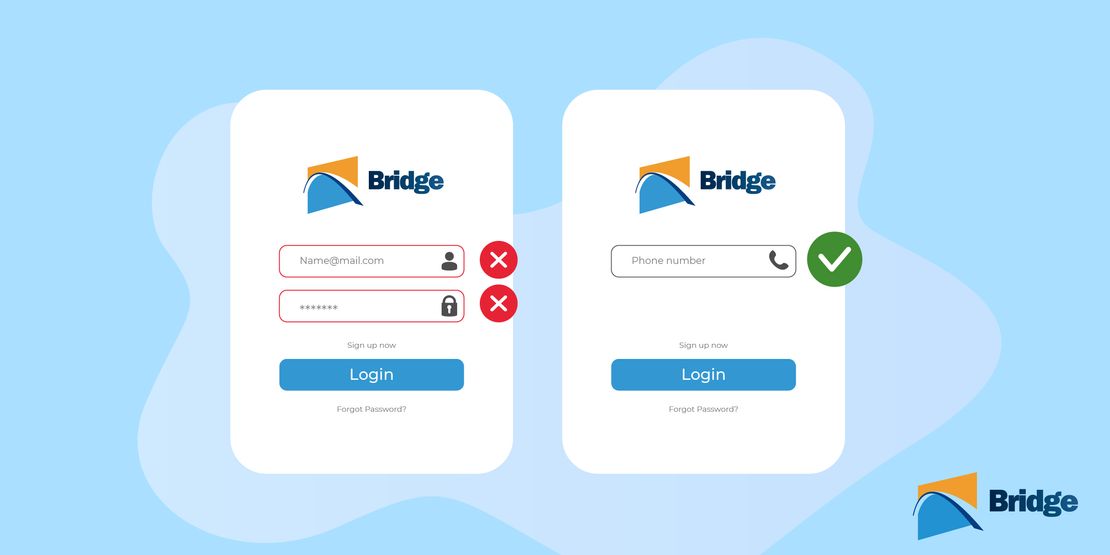
BridgeInteract offers biometric facial recognition for healthcare professionals and patients accessing the platform. This approach ensures that only authorized users can access the system quickly and conveniently. - Phone number login
BridgeInteract sends a unique one-time login code to a user’s phone number to grant quick access without requiring a static password, offering a secure and user-friendly experience. When sharing a phone number (e.g., with family members), the user’s date of birth (DOB) is also requested for authentication. If more than one patient has the same DOB, the user will be prompted to enter their first name. - EHR Integration
BridgeInteract seamlessly integrates with various EHR systems. Providers can access patient records, scheduling systems, and other modules without traditional passwords, making navigating systems easy while maintaining the strictest security standards.
How To Implement Passwordless Authentication In Healthcare Settings
Healthcare organizations looking to implement passwordless authentication solutions should follow these best practices:
- Assess current security needs
Identify which systems and workflows would benefit the most from passwordless technology. - Choose the right authentication methods
Depending on the user base, select methods like biometrics, OTPs, or push notifications that balance security and usability. - Test for compatibility
Ensure that the chosen solution integrates smoothly with existing EHR, RCM, and other healthcare systems. - Implement gradually
Roll out passwordless options gradually, starting with high-risk systems before expanding to other areas. - Educate users
Train healthcare staff and patients on using passwordless methods to ensure a smooth transition.
Of course, working with experienced technicians and trainers can greatly streamline the rollout of new security measures. When you choose a trusted software partner like BridgeInteract, you get an “IT team down the hall” to help you through the process. Our team will work closely with your existing IT personnel to ensure a smooth rollout, establish integrations, solve launch issues, and provide ongoing post-launch support through troubleshooting and maintenance.
Get A Secure Patient Engagement Platform
Passwordless authentication is the future of secure healthcare technology. By removing the vulnerabilities associated with passwords, healthcare providers can enhance security, improve patient engagement, and reduce costs. The BridgeInteract platform leverages advanced passwordless authentication solutions like SSO and biometrics to provide a seamless, secure experience for both patients and providers.
BridgeInteract is SOC 2 certified, demonstrating its adherence to stringent data security standards. Strong encryption, next-generation firewalls, and HIPAA-compliant cloud services are leveraged to protect client data and safeguard patient information.
In addition, BridgeInteract is compliant with the ONC Certification Criteria for Health IT and has been certified by an ONC-ACB in accordance with the applicable certification criteria adopted by the Secretary of Health and Human Services.* To know more about the certified module, please check https://www.bridgeinteract.io/certifications/.
With passwordless technology, BridgeInteract is paving the way for a safer, more efficient healthcare environment that protects sensitive data while providing an unparalleled user experience for all stakeholders.
Discover how BridgeInteract can enhance your healthcare practice
Read more:
- Healthcare Application Security: How to Protect Patient Data
- A Guide To Digital Transformation In Healthcare
- What Digital Tools Should You Offer For Patient Engagement?
*This certification does not represent an endorsement by the US Department of Health and Human Services.
References:
- HIPAA Journal. (2024). Healthcare Data Breach Statistics. Available at: Link. Accessed: 23 October 2024.
- IBM. (2024). Cost of a Data Breach Report. Available at: Link. Accessed: 23 October 2024.
- Barsky, N. (2024). UnitedHealth’s $1.6 Billion Tally Grossly Understates Cyberattack Cost. Forbes. Available at: Link. Accessed: 23 October 2024.
- HIPAA Journal. (2024). What are the Penalties for HIPAA Violations? Available at: Link. Accessed: 23 October 2024.